Terminal Server License Registry
John February 20, 2016 8 Comments on How to reset the Remote Desktop Server Licensing Grace Period on Windows Server 2012 with Remote Desktop Services Licensing Remote Desktop Services So we recently started looking into Terminal Services and RemoteFX to power some of our admin users and move them off to thin clients instead of full blown desktops. Apr 17, 2013 Grace Period has expired even though RD Licensing is properly configured, see Eric Verdumen No remote Desktop Licence Server availible on RD Session Host server 2012. The solution was to delete the REGBINARY in. Sep 09, 2014 Fixes Terminal Server License registry key VB script elevates itself as admin, creates a backup or Terminal Server Licensing Registry key, saves it to users Desktop folder (mslicensebackup.reg), removes the registry key and opens a new RDP connection to specified server (in YOURSERVER-FQDN).Helpfull to solve Citrix termi.
- Terminal Server License Registry Key Windows 7
- Terminal Server 2003 License Registry Key
- Terminal Server License Server Group
- Terminal Server License Expired Registry
Oct 07, 2014 I’ve been asked several times since XenDesktop 7 was released when Windows Server 2012 R1 and R2 were supported operating systems about how can a Remote Desktop Services License server be defined from a application server with a Windows Server 2012 R1 or R2 as the base OS: Remote Desktop licensing mode is not configured. Apr 06, 2019 Remote Desktop Services (Terminal Services) https. In RD Licensing Diagnoser on Server 2016, I get a message that the licensing mode for the Remote Desktop Session Host server is not configured. How does one set this. I cannot find the 'RD Session Host Configuration Tool' like I we have used in the past with Windows Server 2008 R2 to.
Important
Jun 17, 2016 'The remote session was disconnected because there are no Terminal Server License Servers available to provide a license. Please contact the server administrator. The environment was fine but we encountered this before. Apr 17, 2018 The next time the client connects, an attempt is made to upgrade the validated temporary Terminal Server CAL token to a full Terminal Server CAL token. If no license tokens are available, the temporary Terminal Server CAL token will continue to function for 90 days. The license is stored in the client's registry.
This information is intended for administrators and IT Pros. For information about activating a personal copy of Office, see Activate Office.
Shared computer activation lets you to deploy Office 365 ProPlus to a computer in your organization that is accessed by multiple users. Here are some examples of supported scenarios for using shared computer activation:
- Three workers at a factory share a computer, each worker using Office on that computer during their eight-hour shift.
- Fifteen nurses at a hospital use Office on ten different computers throughout the day.
- Five employees connect remotely to the same computer to run Office.
- Multiple employees use Office on a computer that's located in a conference room or some other public space in the company.
The most common shared computer activation scenario is to deploy Office 365 ProPlus to shared computers by using Remote Desktop Services (RDS). By using RDS, multiple users can connect to the same remote computer at the same time. The users can each run Office 365 ProPlus programs, such as Word or Excel, at the same time on the remote computer.
Shared computer activation is used for situations where multiple users share the same computer and the users are logging in with their own account. If you have users who are assigned individual computers and no other users work on those computers, you use product key activation for Office 365 ProPlus.
Normally, users can install and activate Office 365 ProPlus only on a limited number of devices, such as 5 PCs. Using Office 365 ProPlus with shared computer activation enabled doesn't count against that limit.
How to enable shared computer activation for Office 365 ProPlus
If you have an Office 365 plan that includes Office 365 ProPlus, you can use shared computer activation. Make sure you assign each user a license for Office 365 ProPlus and that users log on to the shared computer with their own user account.
Note
Shared computer activation is also available for the following:
- Subscription versions of Project and Visio. For example, if you have the Project Online Professional plan or Visio Online Plan 2.
- Microsoft 365 Business subscribers, whose version of Office is Office 365 Business. But, Microsoft 365 Business subscribers won't be able to use Group Policy to enable shared computer activation, because Office 365 Business doesn't support the use of Group Policy.
Shared computer activation isn't available for Office for Mac.
To enable shared computer activation when you deploy Office 365 ProPlus, you need the current version of the Office Deployment Tool, which is available for free from the Microsoft Download Center.
The Office Deployment Tool, combined with a simple text file, is used to install Office 365 ProPlus on the shared computer, and to enable shared computer activation for that computer. Add the following lines when you create the text file.
After Office 365 ProPlus is installed, you can verify that shared computer activation is enabled on that computer.
Note
If you've already deployed Office 365 ProPlus, you can enable shared computer activation on a computer by using Registry Editor to add a string value of SharedComputerLicensing with a setting of 1 under HKEY_LOCAL_MACHINESOFTWAREMicrosoftOfficeClickToRunConfiguration.
If you're using Microsoft Application Virtualization (App-V) to deploy Office 365 ProPlus, the registry location is HKEY_LOCAL_MACHINESOFTWAREMicrosoftOffice16.0CommonLicensing and it's a DWORD value.
You can also enable shared computer activation by using Group Policy. If you're using Group Policy, download the most current Administrative Template files (ADMX/ADML) for Office and enable the 'Use shared computer activation' policy setting. This policy setting is found under Computer ConfigurationPoliciesAdministrative TemplatesMicrosoft Office 2016 (Machine)Licensing Settings.
How shared computer activation works for Office 365 ProPlus
Here's what happens after Office 365 ProPlus is installed on a computer that has shared computer activation enabled.
A user logs on to the computer with her account.
The user starts an Office 365 ProPlus program, such as Word.
Office 365 ProPlus contacts the Office Licensing Service on the Internet to obtain a licensing token for the user.
To determine whether the user is licensed to use Office 365 ProPlus, the Office Licensing Service has to know the user's account for Office 365. In some cases, Office 365 ProPlus prompts the user to provide the information. For example, the user might see the Activate Office dialog box.
If your environment is configured to synchronize Office 365 and network user accounts, then the user probably won't see any prompts. Office 365 ProPlus should automatically be able to get the necessary information about the user's account in Office 365.
If the user is licensed for Office 365 ProPlus, a licensing token is stored on the computer in the user's profile folder, and Office 365 ProPlus is activated. The user can now use Office 365 ProPlus.
These steps are repeated for each user who logs on to the shared computer. Each user gets a unique licensing token. Just because one user activates Office 365 ProPlus on the computer doesn't mean Office 365 ProPlus is activated for all other users who log on to the computer.
If a user goes to another computer that also is enabled for shared computer activation, the same steps occur. There is a different licensing token for each computer that the user logs on to.
If a user logs on to a shared computer again, Office 365 ProPlus uses the same licensing token, if it is still valid.
Additional details about shared computer activation for Office 365 ProPlus
Licensing token renewal The licensing token that is stored on the shared computer is valid only for 30 days. As the expiration date for the licensing token nears, Office 365 ProPlus automatically attempts to renew the licensing token when the user is logged on to the computer and using Office 365 ProPlus.
If the user doesn't log on to the shared computer for 30 days, the licensing token can expire. The next time that the user tries to use Office 365 ProPlus, Office 365 ProPlus contacts the Office Licensing Service on the Internet to get a new licensing token.
Internet connectivity Because the shared computer has to contact the Office Licensing Service on the Internet to obtain or renew a licensing token, reliable connectivity between the shared computer and the Internet is necessary.
Reduced functionality mode If the user is not licensed for Office 365 ProPlus, or if the user closed the Activate Office dialog box, no licensing token is obtained and Office 365 ProPlus isn't activated. Office 365 ProPlus is now in reduced functionality mode. This means that the user can view and print Office 365 ProPlus documents, but can't create or edit documents. The user also sees a message in Office 365 ProPlus that most features are turned off.
Activation limits Normally, users can install and activate Office 365 ProPlus only on a limited number of devices, such as 5 PCs. Using Office 365 ProPlus with shared computer activation enabled doesn't count against that limit.
Microsoft allows a single user to activate Office 365 ProPlus on a reasonable number of shared computers in a given time period. The user gets an error message in the unlikely event the limit is exceeded.
Single sign-on recommended The use of single sign-on (SSO) is recommended to reduce how often users are prompted to sign in for activation. With single sign-on configured, Office is activated using the user credentials that the user provides to sign in to Windows, as long as the user has been assigned a license for Office 365 ProPlus. For more information, see Understanding Office 365 identity and Azure Active Directory.
If you don't use single sign-on, you should consider using roaming profiles and include the %localappdata%MicrosoftOffice16.0Licensing folder as part of the roaming profile.
Licensing token roaming Starting with Version 1704 of Office 365 ProPlus, you can configure the licensing token to roam with the user's profile or be located on a shared folder on the network. Previously, the licensing token was always saved to a specific folder on the local computer and was associated with that specific computer. In those cases, if the user signed in to a different computer, the user would be prompted to activate Office on that computer in order to get a new licensing token. The ability to roam the licensing token is especially helpful for non-persistent VDI scenarios.
To configure licensing token roaming, you can use either the Office Deployment Tool or Group Policy, or you can use Registry Editor to edit the registry. Whichever method you choose, you need to provide a folder location that is unique to the user. The folder location can either be part of the user's roaming profile or a shared folder on the network. Office needs to be able to write to that folder location. If you're using a shared folder on the network, be aware that network latency problems can adversely impact the time it takes to open Office.
If you're using Group Policy, download the most current Administrative Template files (ADMX/ADML) for Office and enable the 'Specify the location to save the licensing token used by shared computer activation' policy setting. This policy setting is found under Computer ConfigurationPoliciesAdministrative TemplatesMicrosoft Office 2016 (Machine)Licensing Settings.
If you're using the Office Deployment Tool, include the SCLCacheOverride and SCLCacheOverrideDirectory in the Property element of your configuration.xml file. For more information, see Configuration options for the Office Deployment Tool.
To edit the registry, go to HKEY_LOCAL_MACHINESOFTWAREMicrosoftOfficeClickToRunConfiguration, add a string value of SCLCacheOverride, and set the value to 1. Also, add a string value of SCLCacheOverrideDirectory and set the value to the path of the folder to save the licensing token.
Note
If you're using Microsoft Application Virtualization (App-V) to deploy Office 365 ProPlus, the registry location is HKEY_LOCAL_MACHINESOFTWAREMicrosoftOffice16.0CommonLicensing.
Terminal Server License Registry Key Windows 7
Related topics
Registry Keys for Terminal Services
The relevant configuration options for terminal servers, terminal server sessions, users, and clients can be found in different places in the registry. The administration tools and Group Policies, described in the previous chapters, usually change several registry values. The following section provides you with information on their paths and default values.
| Note? | This section is a general overview of those registry keys that are essential for Terminal Services. A full documentation of all relevant keys would probably be a book in its own right. However, if you know where to find the “interesting” locations, there is nothing to prevent you from doing your own experiments on a test system. Experiments have produced many tips for optimizing system performance by modifying the registry, just as described in this book. |
General Settings
We will first examine those areas of the registry that are vital to the global configuration of the terminal server and its sessions. These areas are located in the HKLM root hive.
One of the central HKLM root hive areas can be found under SYSTEMCurrentControlSet and SYSTEMControlSet00n. The numbered ControlSet001 and ControlSet002 subkeys contain control information that is needed to start and keep Windows Server 2003 running. One of these two numbered subkeys is the original; the other is the backup copy. On startup, the system determines which one of the keys is the original and saves the result under HKLMSYSTEMSelect. The last successful set of control information is saved in HKLMSYSTEMCurrentControlSet. The three sets of control information are for the most part identical, but only one is valid and used by the system.
| Note? | In the following, we assume that ControlSet001 contains the valid control information used by the system. On your system, it could be ControlSet002. |
The HKLMSYSTEMControlSet001HKLMSYSTEMControlSet001ControlTerminal Server hive allows you to configure general settings, just as you can under Terminal Services configuration or Group Policies. Some of the values described here will be discussed in detail later in this chapter.
Value Names | Data Type, Default Value | Description |
|---|---|---|
DeleteTempDirsOnExit | DWORD: 0x1 | Deletes temporary session directories when the user logs off. Possible values are 0 or 1. Change this value using the Delete temporary directories on exit server setting in Terminal Services configuration. |
fAllowToGetHelp | DWORD: 0x0 | Disables or enables remote assistance on this computer. Possible values are 0 or 1. Usually, this setting is established in the Remote tab of the Control Panel’s system properties. |
fDenyTSConnections | DWORD: 0x0 | Allows or denies connecting to Terminal Services. Possible values are 0 or 1. |
FirstCountMsgQPeeks-SleepBadApp | DWORD: 0xF | Default value of the compatibility flag for applications. (See “Compatibility Flags” section later in this chapter.) |
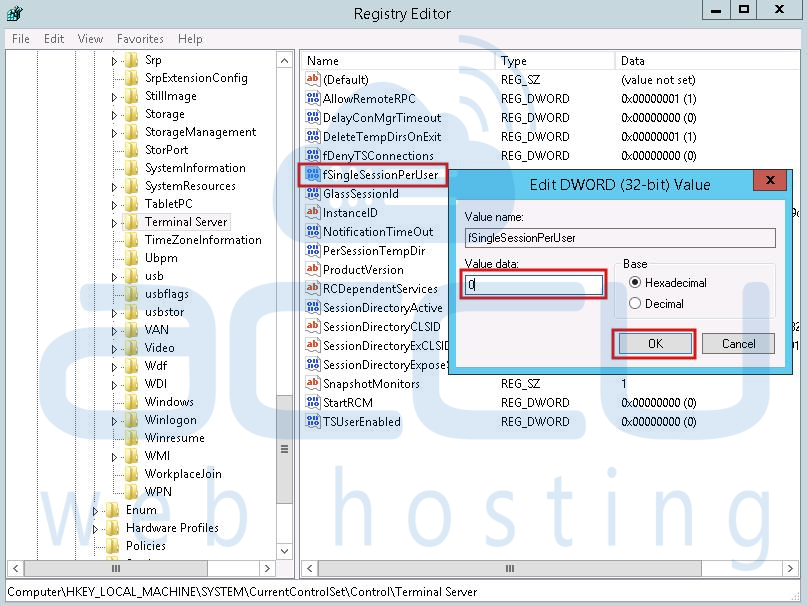
fSingleSessionPerUser | DWORD: 0x1 | Each user can be limited to one session to save server resources or facilitate session recovery. Possible values are 0 or 1. Change this value using the Restrict each user to one session server setting in Terminal Services configuration. |
fWritableTSCCPermTab | DWORD: 0x1 | Allows write-protection of the Permissions tab in the Terminal Services configuration RDP connection settings. Possible values are 0 or 1. |
IdleWinStationPoolCount | DWORD: 0x0 | Sessions started in the background are assigned to new users. The default value for this setting is 0. For application servers, you can select different values, which might reduce login times for new user sessions. |
Modems With Bad DSR | MULTI_SZ | List of modems that have a problem with Data Set Ready (DSR). |
MsgQBadAppSleep-TimeInMillisec | DWORD: 0x1 | Default value of the compatibility flag for applications. (See “Compatibility Flags” section later in this chapter.) |
Hp laserjet 5550 driver. NthCountMsgQPeeksSleepBadApp | DWORD: 0x5 | Default value of the compatibility flag for applications. (See “Compatibility Flags” section later in this chapter.) |
PerSessionTempDir | DWORD: 0x1 | Each user session receives its own temporary directory. Possible values for this setting are 0 or 1. Change this value using the Use per session directory server setting in Terminal Services configuration. |
ProductVersion | SZ: 5.2 | Version number of the terminal server. |
SessionDirectoryActive | DWORD: 0x0 | Indicates whether the session directory for this server is active. Possible values for this setting are 0 or 1. |
SessionDirectoryCLSID | SZ | Class ID, needed by the session directory. |
SessionDirectoryExCLSID | SZ | Another class ID that the session directory needs. |
SessionDirectoryExposeServerIP | DWORD: 0x1 | Indicates whether the server’s IP address is exposed with the activated session directory. Possible values for this setting are 0 or 1. |
TSAdvertise | DWORD: 0x1 | Indicates whether the server advertises itself as the terminal server. Possible values are 0 or 1. |
TSAppCompat | DWORD: 0x1 | Indicates whether the system is running in application compatibility mode. Possible values are 0 or 1. |
TSEnabled | DWORD: 0x1 | Indicates whether basic Terminal Services functions are enabled. Possible values are 0 or 1. |
TSUserEnabled | DWORD: 0x0 | Indicates whether users can log on to the terminal server. Possible values are 0 or 1. |
Figure 6-5: Registry values in the HKLMSYSTEMControlSet001ControlTerminal Server hive.
In addition to individual values, this path holds several subkeys that, in turn, contain keys and values for Terminal Services configuration.
Log and User Session Settings
In Table 6.3, the last elements listed are the Wds and WinStations keys. They play a key role in configuring the RDP protocol and user sessions. Because some keys might exist in several hives, they should be explained in more detail. It is impossible to list and explain all keys in this book, so the following tables show only a selection of the most important configuration options. They can be found in one or more of these registry hives:
HKLMSYSTEMControlSet001ControlTerminal ServerWdsrdpwd
HKLMSYSTEMControlSet001ControlTerminal ServerWdsrdpwdTdstcp
HKLMSYSTEMControlSet001ControlTerminal ServerWinStationConsole
HKLMSYSTEMControlSet001ControlTerminal ServerWinStationConsoleRDP
HKLMSYSTEMControlSet001ControlTerminal Server WinStationRDP-Tcp.
The values here are changed through the tool Terminal Services Configuration.
Table 6.3: The Most Important Subkeys in the HKLMSYSTEMControlSet001HKLMSYSTEMControlSet001ControlTerminal Server Registry Hive Subkeys
Description
AddIns
Configuration of the redirection of clipboard and client ports (redirector)
AuthorizedApplications
Option to configure a list of applications that can be run on the terminal server
ClusterSettings
Configuration of the session directory
DefaultUserConfiguration
All default Terminal Services configuration settings, for example, automatic logon data, time limits, initial program, etc.
Dos
Adjusts DOS shell concerning query of keyboard events
KeyboardTypeMapping
Adjusts keyboard driver for unusual shortcuts or special hardware
SysProcs
A list of system programs that run in the system context (0) or in the user context (1)
Utilities
Adjusts the specific commands for the prompt: Change logon, Change port, Change user, Change winsta, Query appserver, Query process, Query session, Query user, Query winsta, Reset session, and Reset winsta
VIDEO
Device paths for graphics redirection
Wds
Configuration of TCP/IP log settings, for example, delays, buffer attributes, port number, service name, and so on
WinStations
Specific configuration for each type of connection and the console session
Table 6.4 lists the so-called flags. Flags are binary values that make a statement true (1) or false (0).
Value Names (DWORD) | Description |
|---|---|
fAutoClientDrives | Connect to client drives upon logon. |
fAutoClientLpts | Connect to client printers upon logon. |
fDisableCam | Disable client audio mapping. |
fDisableCcm | Disable client COM port mapping. |
fDisableCdm | Disable client drive mapping. |
fDisableClip For the hardcore Wii/GC modders, we have some files here you can't find elsewhere (or is hard to find) on the Internet. For example, we have ISOs of the. Loading Close. Available Free Downloads Roms. Amiga 500/1000 Roms. Wiiware wads google drive. Wii WADs are Wii Channel's from the Wii Shop Channel. × Loading Close. Available Free Downloads. New downloads. 68 rows To install these wads, you'll need the Wad Manager Homebrew App or channel and a custom. Welcome to the home of Wii WADs - WiiWAD.com. Download and install Nintendo Wii Channels using Wii WADs. Roms, Virtual Console and WiiWARE in Wii WADs Torrent before installing Wii Homebrew Apps and WAD files you need to Unlock Your Wii ». | Disable clipboard mapping. |
fDisableCpm | Disable Windows client printer mapping. |
fDisableEncryption | Disable encryption. |
fDisableExe | Disable program start upon connection. |
fDisableLPT | Disable use of printers. |
fEnableWinStation | Enable remote user sessions. |
fForceClientLptDef | Use client main printer by default. |
fInheritAutoClient | Inherit the setting on the terminal server to reset the connection when the connection was ended from another source. |
fInheritAutoLogon | Inherit the setting on the terminal server to use the client’s logon information for automatic logon from another source. |
fInheritCallback | Inherit the setting on the terminal server that a modem calls back from another source. |
fInheritCallbackNumber | Inherit on the terminal server the phone number for modem callback from another source. |
fInheritColorDepth | Inherit the setting on the terminal server for color depth from another source. |
fInheritInitialProgram | Inherit the setting on the terminal server to start an initial program upon logon from another source. |
fInheritMaxDisconnectionTime | Inherit on the terminal server the maximum time after which disconnected sessions are ended from another source. |
fInheritMaxIdleTime | Inherit on the terminal server the maximum idle time for user sessions from another source. |
fInheritMaxSessionTime | Inherit on the terminal server the maximum session time from another source. |
fInheritReconnectSame | Inherit the setting on the terminal server whether a new connection can be made only from the same client from another source. |
fInheritResetBroken | Inherit the setting on the terminal server, whether the session is ended upon reaching a session limit or upon disconnection from another source. If you do not set this flag, the session will be simply disconnected. |
fInheritSecurity | Inherit the security setting on the terminal server. |
fInheritShadow | Inherit the setting on the terminal server for remote control from another source. |
fLogonDisabled | Selecting this flag disables logon. |
fPromptForPassword | Makes entering a password obligatory. |
fReconnectSame | You can reconnect from the same client only as you did previously. This value becomes effective only if you set the fInheritReconnectSame flag. |
fResetBroken | The session ends when a session limit is reached or the connection is broken. If this flag is not set, the session is simply disconnected. This value becomes effective only if you set the fInheritResetBroken flag. |
fUseDefaultGina | Always use the default Windows component to authenticate users. |
Table 6.5 lists the most important keys with the REG_DWORD data type. These are often directly related to one of the flags listed in the preceding table.
Value Names (DWORD) | Description |
|---|---|
Callback | Set modem callback. This value becomes effective only if you set the fInheritCallback flag to 0. |
ColorDepth | Default color-depth setting. |
DrawGdiplusSupportLevel | Support options for graphics elements output with GDI+. |
InputBufferLength | Input buffer length for the RDP connection in bytes. Default value is 2048. |
KeyboardLayout | Set keyboard layout. |
MaxConnectionTime | Maximum session time in seconds. This value becomes effective only if you set the fInheritMaxSessionTime flag to 0. |
MaxDisconnectionTime | Maximum time in seconds after which disconnected sessions are ended. This value becomes effective only if you set the fInheritMaxDisconnectionTime flag to 0. |
MaxIdleTime | Maximum idle time in seconds for user sessions. This value becomes effective only if you set the fInheritMaxIdleTime flag to 0. |
MinEncryptionLevel | Set the minimum value of encryption level. |
OutBufDelay | Maximum waiting time in milliseconds until the output buffer for the RDP connection is emptied. |
OutBufLength | Output buffer length for the RDP connection in bytes. |
PortNumber | Port for network communication using the RDP protocol. Default value is 3398. |
Shadow | Remote control configuration. This value becomes effective only if you set the fInheritShadow flag to 0. |
Finally, Table 6.6 shows the most important keys of the REG_SZ data type.
Value Names (SZ) | Description |
|---|---|
CallbackNumber | Set a phone number for modem callback. This value becomes effective only if you set the fInheritCallbackNumber flag to 0. |
Comment | Comment string in the administration tool. |
Domain | Set a default domain name on logon of a user session. |
InitialProgram | Initial program that is started when a user logs on. This value becomes effective only if you set the fInheritInitialProgram flag. |
NWLogonServer | Set a NetWare logon server. |
Password | Set a default password when logging on to a user session. The password is encrypted and saved here. |
UserName | Set a default user name for logon to a user session. |
WorkDirectory | Working directory that is set on user logon and initial start of an application. |
Drivers and Services
The HKLMSYSTEMControlSet001ServicesTermDD hive contains the attributes of the Termdd.sys terminal device driver. However, do not change these attributes. You can find the device driver’s path and start option here.
An adjoining hive, called HKLMSYSTEMControlSet001ServicesTermService, hosts both the configuration of Terminal Services within the generic Svchost.exe Windows service and of the Services.exe process. The keys you find there include, for example, the display name, description, complete path, or start options as also listed under services administration. The subkeys show license settings and parameters for the performance indicator object of the system monitor.
Figure 6-6: Drivers and services for terminal server functions.
| Note? | The UseLicenseServer key under Parameters is used by Windows NT 4.0, Terminal Server Edition. Windows Server 2003 no longer needs this key. It remains in the registry for compatibility reasons only. |
Logon
If you log registry access in a focused manner during logon of a user session, you will gain interesting insights into the corresponding initialization processes. For example, which areas relevant for terminal servers does the Winlogon.exe logon process access?
One piece of information needed during logon concerns creating or loading the user profile. HKLMSOFTWAREMicrosoftWindows NTCurrentVersionProfileList. These keys contain the default paths for a default user (DefaultUser), general user (AllUsers), and individual user profiles. Furthermore, you can find a list of all users who have logged on to the system here. If a user logs on to the terminal server for the first time, he or she inherits both the normal default user settings and the default values for the terminal server session. They are saved under HKLMSYSTEMControlSet001HKLMSYSTEMControlSet001ControlTerminal ServerDefaultUserConfiguration.
Another relevant area is located under HKLMSoftwareMicrosoftWindows NTCurrentVersionWinlogon. It includes the AppSetup key that defines a special script file called UsrLogon.cmd. This script file is executed along with a possible logon script on startup of each terminal server session. (See Chapter 7.) The same location also contains the WinStationDisabled key that either denies (0) or allows (1) new terminal server users to log on, regardless of the protocol. At the prompt, you can modify this value using the Change logon /enable or Change logon /disable prompts.
Terminal Server 2003 License Registry Key
The HKLMSoftwareMicrosoftWindows NTCurrentVersionWinlogonNotifytermsrv area is also needed for logon. It defines a specific logic as a response to system events.
Figure 6-7: Determining the response to system events.
When a user logs on, even driver configuration is accessed. The area reserved for terminal servers is located under HKLMSOFTWAREMicrosoftWindows NTCurrentVersionDrivers32Terminal ServerRDP. The video driver configuration plays a certain role for the user session, too. For instance, Explorer.exe needs the corresponding data that is located here: HKLMSYSTEMControlSet001HKLMSYSTEMControlSet001ControlTerminal ServerVIDEOrdpdd under the DeviceVideo0 key.
If local Group Policies for Terminal Services settings were established, these must be loaded at the right time, of course. This happens during logon with keys found under HKLMSOFTWAREPoliciesMicrosoftWindows NTTerminal Services and the EnableAdminTSRemote key under HKLMSOFTWAREPoliciesMicrosoftWindowsInstaller. However, these areas can be fairly empty if no or just a few local Group Policies were predefined.
| Note? | Basically, the settings for local Group Policies are located under HKCUSoftwarePolicies and HKLMSOFTWAREPolicies. Users have only read-access rights to these two hives. Therefore, Group Policies cannot be modified at the user level. |
Terminal Server License Server Group
Printing
Connecting and managing printers for terminal servers is a very complex topic. (See Chapter 4.) This fact is also quite evident in the registry. The general configuration of the printers used and the associated driver information are located under HKLMSystemCurrentControlSetControlPrint.
Terminal Server License Expired Registry
You will find references to the currently installed printer drivers of the terminal server under HKLMSYSTEMControlSet001ControlPrintEnvironmentsWindowsNTx86DriversVersion-3<Printer name>. This correlates with the files under %SystemRoot%system32spooldriversw32x863. The user-specific settings for the printers are located in the registry under HKCUPrinters.
| Note? | Information for the printer drivers for the Windows Server 2003 64 bit versions is located under HKLMSYSTEMControlSet001ControlPrint EnvironmentsWindowsIA64Drivers. |
If you do not want to install printer drivers from sources that might not be controllable, you have the option of choosing a binding path. This path is called a trusted printer driver path. To configure this behavior, you need to add the following keys to HKLMSYSTEMControlSet001ControlPrintProvidersLanManPrintServicesservers:
Name: LoadTrustedDrivers; type: REG_DWORD; value: 1
Name: TrustedDriverPath; type: REG_SZ; value: Server nameShare folder
It is important that the structure of the Server nameShare folder mirror the %SystemRoot%system32spooldriversw32x86 folder. If all the data was properly entered, printer drivers can be installed only from the predefined source, allowing complete control of the printer drivers used.
User-Specific Configuration
The registry’s user-specific section also contains keys that are relevant to the terminal server. For example, the HKCUSoftwareMicrosoftWindows NTCurrentVersionTerminal Server hive has the key called LastUserIniSyncTime. This key indicates the last system time a user-specific .ini file was synchronized to its corresponding system-wide .ini file (discussed later in this chapter).
If a user has administrator permissions, there is an additional key called TSADMIN here, containing several subkeys. These subkeys allow access to attributes for connection options, alerts, refresh rates, keyboard shortcuts for remote control, server list options, and display values for system processes in the Task Manager.
Figure 6-9: User-specific terminal server settings for an administrator.
After a user session has been established, it has its own ID (SESSIONNAME). It is located next to the client name (CLIENTNAME) and the logon server name (LOGONSERVER) in the HKCUVolatile Environment section of the registry.
Use the following registry sections to define all relevant user folders in which to save data about the applications, desktop, local settings, personal files, network environment, print environment, or start menu:
HKCUSOFTWAREMicrosoftWindowsCurrentVersionExplorerUser Shell Folders
HKLMSOFTWAREMicrosoftWindowsCurrentVersionExplorerUser Shell Folders